Protect Corporate Data in Network Operations Center
Microsoft Teams Monitoring
Why the NOC and SOC must work together
Within an organization, the Network Operations Center (NOC) and Security Operations Center (SOC) teams need to work together to maintain optimal Microsoft Teams performance network performance in addition to ensuring both overall security and the availability of IT services for business lines.
In the past, these two teams were focused on two separate objectives, using different tools to do so and often running specific processes. What we have seen recently is the increased need for the convergence of the NOC and SOC teams – and many of their processes – when it comes to certain levels of support or specific incident remediation.
There are multiple factors that impacted this trend. For example, the growth of mobile access points have led cyberattacks to diversify their attack strategy, jumping between different types of IT equipment to cover their tracks and to launch new forms of attacks. The complexity of threats such as the Stuxnet worm has really shown that both the production and security teams need to work together to better identify and stop these kinds of attacks.
We think that you don’t need a malicious threat though to realize that collaboration between the SOC and NOC teams has many advantages. How many times have you heard of or been a part of a ‘finger pointing’ session between the security and operations teams regarding an event that ultimately affected the business lines and significantly impacted company efficiency? Probably more than once!
This situation is not uncommon – we see this within any organization that we work with. Security events can sometimes involve both network performance and availability issues. When this occurs, both teams need to work together to resolve these problems. A common example of this would be when a new firewall rule is implemented by the SOC team that can end up blocking traffic. On the flip side, for the NOC team, a network event can also appear to be a security threat. For example, we see a lot of businesses have a period that sees a dramatic increase in inbound website hits. This activity can often be seen as a threat such as a distributed denial-of-service (DDoS) attack.
If the NOC and SOC teams are working in silos and nothing is done to help both teams quickly collaborate to qualify an event, the lack of visibility and lack of communication can end up hurting both teams. This results in increased response time when an incident occurs and provides ample room for a cyber-attack which can be dramatically more damaging and costly to fix.
So what can be done for Microsoft Teams performance?
Fortunately, there are several new ways to improve this situation. For example, last year Gartner indicated that 60% of enterprises have reported that they will have a SASE (Secure Access Service Edge) strategy in place by 2025 and the rise of SOAR (Security, Orchestration, Automation and Response) is also helping companies.
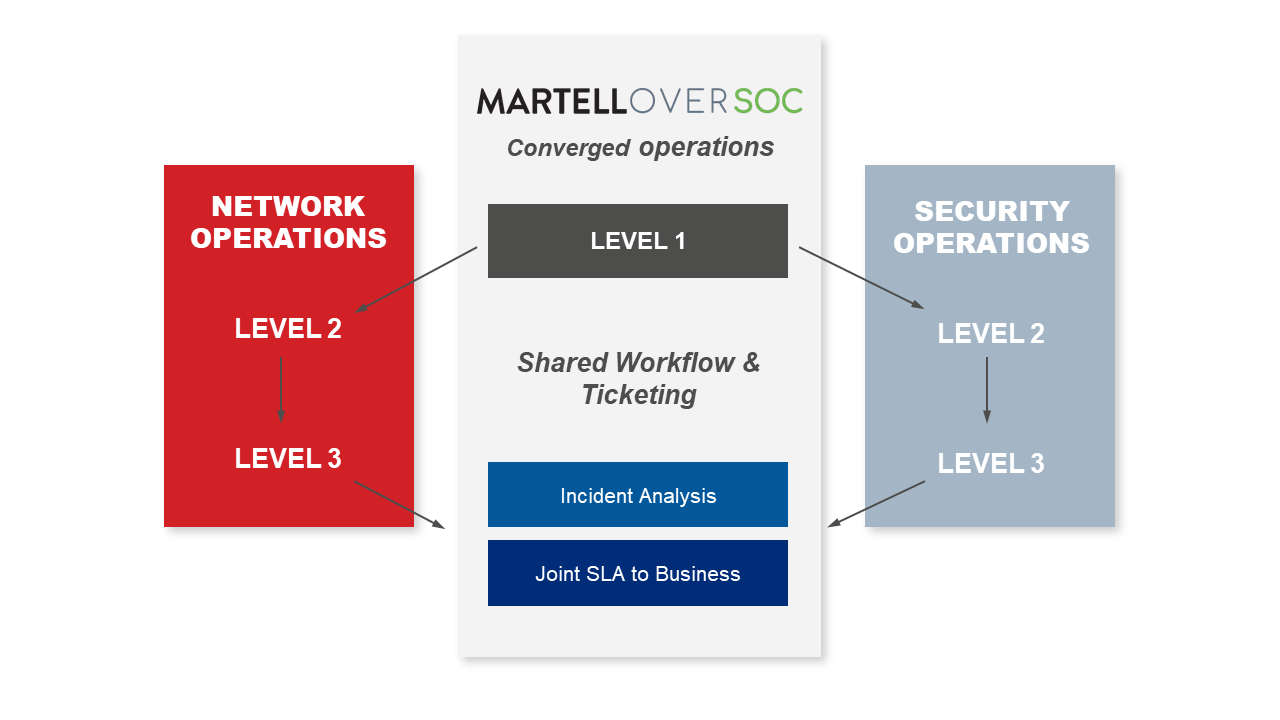
To improve the situation, you don’t have to merge the NOC and SOC. The primary focus should be to break down the silos to enable them to better work together: Close collaboration is often enough to achieve efficiency goals without fully integrating or merging (Gartner).
Breaking Down the Silos: 3 Main Areas of Focus
Organizational: shared standard operation procedures for level 1 support are needed to identify and qualify both incidents and threats.
Tools: provide a shared ticketing system and shared service level agreement.
Assets: with a common information aggregator to collect and distribute the data.
Next Steps
Martello and OverSOC have merged their collection and data correlation capabilities from both production and security environments to provide an enterprises ‘IT with a simple and efficient solution that allows tier 1 event monitoring for both NOC and SOC. This means that the NOC and SOC teams can easily share the same monitoring data to unify alert monitoring and response functions all while integrating them automatically with a common ticketing or ITSM toolset.