What is Internet Control Message Protocol (ICMP)?
Microsoft Teams Monitoring
With so many organizations focused on locking down environments, protocols like ICMP get immediately blocked without first weighing out the benefits.
What is ICMP
If you’ve ever used the Ping or Tracert command, you’ve taken advantage of the Internet Control Message Protocol (ICMP). ICMP was designed to allow network admins to perform diagnostic tests and troubleshoot problems by understanding whether network destinations were unreachable or if latency exists on specific segments along the way. For example, ICMP can be used to determine jitter, round-trip time (RTT), and packet loss details which can provide valuable insight into the network quality of specific segments of a network packet’s path from source to destination.
Originally, there were 255 requests and responses used by ICMP, with only ten remaining relevant today (shown below).
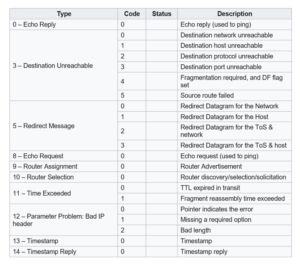
Source: Wikipedia
In recent years, due to cybersecurity concerns, many network teams have simply blocked ICMP completely without understanding how this break legitimate (and needed) functionality.
So, what are the real risks of leaving ICMP enabled?
What is the risk of allowing ICMP
As with any protocol, platform, operating system, service, and application, threat actors have looked for ways to take advantage of the environment they are attacking, finding ways to further their ability to maintain a connection, transfer data, communicate with a Command & Control server, etc. In the case of ICMP, threat actors have found ways to misuse ICMP:
Ping of Death
- This was the first example of ICMP being widely misused. This malformed Ping request could result in the crash of a machine. Updates to the protocol have subsequently rendered this attack useless. Ping floods (i.e., a rapid succession of ping requests) are still possible today, although firewalls should detect and stop these.
ICMP Tunneling
- Malicious communications and data can be transmitted within ICMP packets, bypassing firewall rules. But keep in mind that data tunneling over other protocols (e.g., HTTPS, DNS) commonly exist today as well, making this a diminished concern specific to ICMP.
Ping sweeps
- Threat actors can use simple ping requests across entire subnets to enumerate hosts on a network. Again, firewalls should be able to detect and stop these, unless the threat actor is sweeping the same subnet as a compromised endpoint (in which case, firewall rules don’t apply anyway).
While ICMP can be misused, it’s evident that most malicious actions via ICMP are no longer a threat and have been rendered useless in today’s networks.
In addition, ICMP still remains useful today.
Benefits of ICMP
Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. Admins use these messages to troubleshoot network connectivity issues. A great example is that of either a gateway or destination host sending an ICMP message to the source host if there is an error or a change in network connectivity that requires notification – such as a destination host or networking being unreachable, packet loss during transmission, etc.
Additionally, solutions focused on monitoring the network for connectivity and performance reasons often leverage ICMP as a means to determine the presence of issues requiring attention of the network team. ICMP requests and responses prove to be an invaluable, fast, and simple way to test connectivity and help to determine the root cause of any network delivery and performance issues.
So, how can you strike a balance between enabling ICMP and maintaining a secure environment?
Improving monitoring and troubleshooting while securing your network
There needs to be a balance here between the need for a secure network and enabling admins and monitoring solutions. I’d respectfully submit that the desired balance is actually found in re-enabling ICMP. In other words, there’s no reason to block it.
In essence, the act of blocking ICMP is in response to a desire to thwart covert malicious communication. Given that this can take place across any of a number of other protocols, the only reason to block ICMP is if no one is using it legitimately.
But, since admins can leverage ICMP requests to test the network, and monitoring solutions can take advantage of ICMP to continually watch the state of system, service, application, and network availability, it simply doesn’t make sense to limit the use of ICMP.
About Martello:
Martello provides the only end-to-end Microsoft Teams performance monitoring tool that Microsoft recommends to their customers to maximize employee productivity.
Our solution Vantage DX proactively monitors Microsoft 365 and Teams service quality, enabling IT with complete visibility of the user experience to ease troubleshooting of issues before they impact users.
Find out why Martello is Microsoft’s go-to-solution for Microsoft Office 365 Monitoring >>


